What is CTR?
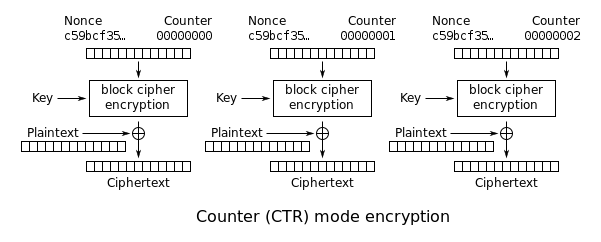
Overview
CTR (short for counter) is a popular
In the CTR mode, we start off with a random seed, s, and compute pad vectors according to the formula:
Now that the vectors have been generated, encryption similar to the OFB mode can proceed using the following formula:
Decryption is carried out in a similar way:
Note: CTR, like the CFB and OFB modes, also makes use of a single encryption algorithm for both encryption and decryption.
Advantages and disadvantages of using the CTR mode
Since blocks are independent of one another with the CTR mode, once the pad vectors have been generated, both encryption and decryption of blocks can be parallelly done. The lack of interdependency also means that the CTR mode is tolerant to a loss in blocks. The CTR mode is considered to be very secure and efficient for most purposes.
A serious disadvantage of the CTR is that a synchronous counter needs to be maintained at both receiving and sending ends. Losing track of this counter could lead to the incorrect recovery of plaintext.
CTR encryption using OpenSSL
The OpenSSL toolkit provides a set of simple commands to encrypt using AES modes. The template command for encrypting a 128-bit AES with CTR mode is:
openssl enc -aes-128-ctr -e -in inputfile.txt -out cipher.bin -K
00112233445566778889aabbccddeeff -iv 0102030405060708
In the command above, we will enter the name of the file we want to encrypt after the -in flag, and the name and format of the output file after the -out flag. The hex value of the encryption key should be provided after the -K flag, and the hex value of the initialization vector should be provided after the -iv flag.
Free Resources